-->
Note
This article is intended for technical support agents and IT professionals. If you're looking for more information about Windows activation error messages, see Get help with Windows activation errors.
This article provides troubleshooting information to help you respond to error messages that you may receive when you try to use a Multiple Activation Key (MAK) or the Key Management Service (KMS) to perform Volume Activation on one or more Windows-based computers. Look for the error code in the following table, and then select the link to see more information about that error code and how to resolve it.
For more information about volume activation, see Plan for volume activation.
Cara Menghilangkan Windows License Is Expired Build 9200 0xc004d302 Slui.exe 0x2a 0xc004d302 Microsoft Windows Core. Download Ulead Videostudio 11 Portable Gratis Full. Windows 10 Re-Activate Licence Key with Error Code 0xC004d302.
For more information about volume activation for current and recent versions of Windows, see Volume Activation [client].
For more information about volume activation for older versions of Windows, see KB 929712, Volume Activation information for Windows Vista, Windows Server 2008, Windows Server 2008 R2 and Windows 7.
Diagnostic tool
Note

This tool is intended to help fix Windows activation problems on computers that run Enterprise, Professional, or Server edition of Windows.
Microsoft Support and Recovery Assistant (SaRA) simplifies Windows KMS Activation troubleshooting. Download the diagnostic tool from here.
This tool will try to activate Windows. If it returns an activation error code, the tool will display targeted solutions for known error codes.
The following error codes are supported: 0xC004F038, 0xC004F039, 0xC004F041, 0xC004F074, 0xC004C008, 0x8007007b, 0xC004C003, 0x8007232B.
Summary of error codes
| Error code | Error message | Activation type |
|---|---|---|
| 0x8004FE21 | This computer is not running genuine Windows. | MAK KMS client |
| 0x80070005 | Access denied. The requested action requires elevated privileges. | MAK KMS client KMS host |
| 0x8007007b | 0x8007007b DNS name does not exist. | KMS client |
| 0x80070490 | The product key you entered didn't work. Check the product key and try again, or enter a different one. | MAK |
| 0x800706BA | The RPC server is unavailable. | KMS client |
| 0x8007232A | DNS server failure. | KMS host |
| 0x8007232B | DNS name does not exist. | KMS client |
| 0x8007251D | No records found for DNS query. | KMS client |
| 0x80092328 | DNS name does not exist. | KMS client |
| 0xC004B100 | The activation server determined that the computer could not be activated. | MAK |
| 0xC004C001 | The activation server determined the specified product key is invalid | MAK |
| 0xC004C003 | The activation server determined the specified product key is blocked | MAK |
| 0xC004C008 | The activation server determined that the specified product key could not be used. | KMS |
| 0xC004C020 | The activation server reported that the Multiple Activation Key has exceeded its limit. | MAK |
| 0xC004C021 | The activation server reported that the Multiple Activation Key extension limit has been exceeded. | MAK |
| 0xC004F009 | The Software Protection Service reported that the grace period expired. | MAK |
| 0xC004F00F | The Software Licensing Server reported that the hardware ID binding is beyond level of tolerance. | MAK KMS client KMS host |
| 0xC004F014 | The Software Protection Service reported that the product key is not available | MAK KMS client |
| 0xC004F02C | The Software Protection Service reported that the format for the offline activation data is incorrect. | MAK KMS client |
| 0xC004F035 | The Software Protection Service reported that the computer could not be activated with a Volume license product key. | KMS client KMS host |
| 0xC004F038 | The Software Protection Service reported that the computer could not be activated. The count reported by your Key Management Service (KMS) is insufficient. Please contact your system administrator. | KMS client |
| 0xC004F039 | The Software Protection Service reported that the computer could not be activated. The Key Management Service (KMS) is not enabled. | KMS client |
| 0xC004F041 | The Software Protection Service determined that the Key Management Server (KMS) is not activated. KMS needs to be activated. | KMS client |
| 0xC004F042 | The Software Protection Service determined that the specified Key Management Service (KMS) cannot be used. | KMS client |
| 0xC004F050 | The Software Protection Service reported that the product key is invalid. | MAK KMS KMS client |
| 0xC004F051 | The Software Protection Service reported that the product key is blocked. | MAK KMS |
| 0xC004F064 | The Software Protection Service reported that the non-genuine grace period expired. | MAK |
| 0xC004F065 | The Software Protection Service reported that the application is running within the valid non-genuine period. | MAK KMS client |
| 0xC004F06C | The Software Protection Service reported that the computer could not be activated. The Key Management Service (KMS) determined that the request timestamp is invalid. | KMS client |
| 0xC004F074 | The Software Protection Service reported that the computer could not be activated. No Key Management Service (KMS) could be contacted. Please see the Application Event Log for additional information. | KMS client |
Causes and resolutions
0x8004FE21 This computer is not running genuine Windows
Possible cause
This issue can occur for several reasons. The most likely reason is that language packs (MUI) have been installed on computers that are running Windows editions that are not licensed for additional language packs.
Note
This issue is not necessarily an indication of tampering. Some applications can install multi-lingual support even when that edition of Windows is not licensed for those language packs.)
This issue may also occur if Windows has been modified by malware to allow additional features to be installed. This issue may also occur if certain system files are corrupted.
Resolution
To resolve this issue, you must reinstall the operating system.
0x80070005 Access denied
The full text of this error message resembles the following:
Access denied. The requested action requires elevated privileges.
Possible cause
User Account Control (UAC) prohibits activation processes from running in a non-elevated Command Prompt window.
Resolution
Run slmgr.vbs from an elevated command prompt. To do this, on the Start menu, right-click cmd.exe, and then select Run as administrator.
0x8007007b DNS name does not exist
Possible cause
This issue may occur if the KMS client cannot find the KMS SRV resource records in DNS.
Resolution
For more information about troubleshooting such DNS-related issues, see Common troubleshooting procedures for KMS and DNS issues.
0x80070490 The product key you entered didn't work
The full text of this error resembles the following:
The product key that you entered didn't work. Check the product key and try again, or enter a different one.
Possible cause
This issue occurs because the MAK that was entered was not valid, or because of a known issue in Windows Server 2019.
Resolution
To work around this issue and activate the computer, run slmgr -ipk <5x5 key> at an elevated command prompt.
0x800706BA The RPC server is unavailable
Possible cause
Firewall settings are not configured on the KMS host, or DNS SRV records are stale.
Resolution
On the KMS host, make sure that a firewall exception is enabled for the Key Management Service (TCP port 1688).
Make sure that the DNS SRV records point to a valid KMS host.
Troubleshoot network connections.

For more information about troubleshooting such DNS-related issues, see Common troubleshooting procedures for KMS and DNS issues.
0x8007232A DNS server failure
Possible cause
The system has network or DNS issues.
Resolution
Troubleshoot network and DNS.
0x8007232B DNS name does not exist
Possible cause
The KMS client cannot find KMS server resource records (SRV RRs) in DNS.
Resolution
Verify that a KMS host has been installed and DNS publishing is enabled (default). If DNS is unavailable, point the KMS client to the KMS host by using slmgr.vbs /skms <kms_host_name>.
If you do not have a KMS host, obtain and install an MAK. Then, activate the system.
For more information about troubleshooting such DNS-related issues, see Common troubleshooting procedures for KMS and DNS issues.
0x8007251D No records found for DNS query
Possible cause
The KMS client cannot find KMS SRV records in DNS.
Resolution
Troubleshoot network connections and DNS. For more information about how to troubleshoot such DNS-related issues, see Common troubleshooting procedures for KMS and DNS issues.
0x80092328 DNS name does not exist
Possible cause
This issue may occur if the KMS client cannot find the KMS SRV resource records in DNS.
Resolution
For more information about troubleshooting such DNS-related issues, see Common troubleshooting procedures for KMS and DNS issues.
0xC004B100 The activation server determined that the computer could not be activated
Possible cause
The MAK is not supported.
Resolution
To troubleshoot this issue, verify that the MAK that you are using is the MAK that was provided by Microsoft. To verify that the MAK is valid, contact the Microsoft Licensing Activation Centers.
0xC004C001 The activation server determined the specified product key is invalid
Possible cause
The MAK that you entered is not valid.
Resolution
Verify that the key is the MAK that was provided by Microsoft. For additional assistance, contact the Microsoft Licensing Activation Centers.
0xC004C003 The activation server determined the specified product key is blocked
Possible cause
The MAK is blocked on the activation server.
Resolution
To obtain a new MAK, contact the Microsoft Licensing Activation Centers. After you obtain the new MAK, try installing and activating Windows again.
0xC004C008 The activation server determined that the specified product key could not be used
Possible cause
The KMS key has exceeded its activation limit. A KMS host key can be activated up to 10 times on up to six different computers.
Resolution
If you require additional activations, contact the Microsoft Licensing Activation Centers.
0xC004C020 The activation server reported that the Multiple Activation Key has exceeded its limit
Possible cause
The MAK has exceeded its activation limit. By design, MAKs can be activated a limited number of times.
Resolution
If you require additional activations, contact the Microsoft Licensing Activation Centers.
0xC004C021 The activation server reported that the Multiple Activation Key extension limit has been exceeded
Possible cause
The MAK has exceeded its activation limit. By design, MAKs activate a limited number of times.
Resolution
If you need additional activations, contact the Microsoft Licensing Activation Centers.
0xC004F009 The Software Protection Service reported that the grace period expired
Possible cause
The grace period expired before the system was activated. Now, the system is in the Notifications state.
Resolution
For assistance, contact the Microsoft Licensing Activation Centers.
0xC004F00F The Software Licensing Server reported that the hardware ID binding is beyond level of tolerance
Possible cause
The hardware has changed or the drivers were updated on the system.
Resolution
If you are using MAK activation, use either online or phone activation to reactivate the system during the OOT grace period.
If you are using KMS activation, restart Windows or run slmgr.vbs /ato.
0xC004F014 The Software Protection Service reported that the product key is not available
Possible cause
No product keys are installed on the system.
Resolution
If you are using MAK activation, install a MAK product key.
If you are using KMS activation, check the Pid.txt file (located on the installation media in the sources folder) for a KMS Setup key. Install the key.
0xC004F02C The Software Protection Service reported that the format for the offline activation data is incorrect
Possible cause
The system has detected that the data entered during phone activation is not valid.
Resolution
Verify that the CID is entered correctly.
0xC004F035 Invalid Volume License Key
The full text of this error message resembles the following:
Error: Invalid Volume License Key. In order to activate, you need to change your product key to a valid Multiple Activation Key (MAK) or Retail key. You must have a qualifying operating system license AND a Volume license Windows 7 upgrade license, or a full license for Windows 7 from a retail source. ANY OTHER INSTALLATION OF THIS SOFTWARE IS IN VIOLATION OF YOUR AGREEMENT AND APPLICABLE COPYRIGHT LAW.
The error text is correct, but is ambiguous. This error indicates that the computer is missing a Windows marker in its BIOS that identifies it as an OEM system that is running a qualifying edition of Windows. This information is required for KMS client activation. The more specific meaning of this code is 'Error: Invalid Volume License Key'
Possible cause
Windows 7 Volume editions are licensed only for upgrade. Microsoft does not support installing a Volume operating system on a computer that does not have a qualifying operating system installed.
Resolution
In order to activate, you need to do one of the following:
- Change your product key to a valid Multiple Activation Key (MAK) or Retail key. You must have a qualifying operating system license AND a Volume license Windows 7 upgrade license, or a full license for Windows 7 from a retail source.
Note
If you receive error 0x80072ee2 when you attempt to activate, use the phone activation method that follows instead.
- Activate by phone by following these steps:
- Run slmgr /dti and then record the value of the Installation ID.
- Contact the Microsoft Licensing Activation Centers and provide the Installation ID in order to receive a Confirmation ID.
- To activate by using the Confirmation ID, run slmgr /atp <Confirmation ID>.
0xC004F038 The count reported by your Key Management Service (KMS) is insufficient
The full text of this error message resembles the following:
The Software Protection Service reported that the computer could not be activated. The count reported by your Key Management Service (KMS) is insufficient. Please contact your system administrator.
Possible cause
The count on the KMS host is not high enough. For Windows Server, the KMS count must be greater than or equal to 5. For Windows (client), the KMS count must be greater than or equal to 25.
Resolution
Before you can use KMS to activate Windows, you must have more computers in the KMS pool. To obtain the current count on the KMS host, run Slmgr.vbs /dli.
0xC004F039 The Key Management Service (KMS) is not enabled
The full text of this error message resembles the following:
The Software Protection Service reported that the computer could not be activated. The Key Management Service (KMS) is not enabled.
Possible cause
KMS did not respond to the KMS request.
Resolution
Troubleshoot the network connection between the KMS host and the client. Make sure that TCP port 1688 (default) is not blocked by a firewall or is otherwise filtered.
0xC004F041 The Software Protection Service determined that the Key Management Server (KMS) is not activated
The full text of this error message resembles the following:
The Software Protection Service determined that the Key Management Server (KMS) is not activated. KMS needs to be activated.
Possible cause
The KMS host is not activated.
Resolution
Activate the KMS host by using either online or telephone activation.
0xC004F042 The Software Protection Service determined that the specified Key Management Service (KMS) cannot be used
Possible cause
This error occurs if the KMS client contacted a KMS host that could not activate the client software. This can be common in mixed environments that contain application-specific and operating system-specific KMS hosts, for example.
Resolution
Make sure that if you use specific KMS hosts to activate specific applications or operating systems, the KMS clients connect to the correct hosts.
0xC004F050 The Software Protection Service reported that the product key is invalid
Possible cause
This can be caused by a typo in the KMS key or by typing in a Beta key on a Released version of the operating system.
Resolution
Windows Activation Error 0xc004d302
Install the appropriate KMS key on the corresponding version of Windows. Check the spelling. If the key is being copied and pasted, make sure that em-dashes were not substituted for the hyphens in the key.
0xC004F051 The Software Protection Service reported that the product key is blocked
Possible cause
The activation server determined that Microsoft has blocked the product key.
Resolution
Obtain a new MAK or KMS key, install it on the system, and activate.
0xC004F064 The Software Protection Service reported that the non-genuine grace period expired
Possible cause
Windows Activation Tools (WAT) has determined that the system is not genuine.
Resolution
For assistance, contact the Microsoft Licensing Activation Centers.
0xC004F065 The Software Protection Service reported that the application is running within the valid non-genuine period
Possible cause
Windows Activation Tools has determined that the system is not genuine. The system will continue to run during the Non-Genuine grace period.
Resolution
Obtain and install a genuine product key, and activate the system during the grace period. Otherwise, the system will go into the Notifications state at the end of the grace period.
0xC004F06C The request timestamp is invalid
The full text of this error message resembles the following:
The Software Protection Service reported that the computer could not be activated. The Key Management Service (KMS) determined that the request timestamp is invalid.
Possible cause
The system time on the client computer is too different from the time on the KMS host. Time sync is important to system and network security for a variety of reasons.
Resolution
Fix this issue by changing the system time on the client to sync with the KMS host. We recommend that you use a Network Time Protocol (NTP) time source or Active Directory Domain Services for time synchronization. This issue uses UTP time and does not depend on Time Zone selection.
0xC004F074 No Key Management Service (KMS) could be contacted
The full text of this error message resembles the following:
The Software Protection Service reported that the computer could not be activated. No Key Management Service (KMS) could be contacted. Please see the Application Event Log for additional information.
Possible cause
All of the KMS host systems returned an error.
Resolution
In the Application Event Log, identify each event that has Event ID 12288 and is associated with the activation attempt. Troubleshoot the errors from these events.
For more information about troubleshooting DNS-related issues, see Common troubleshooting procedures for KMS and DNS issues.
-->Updated: February 23, 2016
Applies To: Windows 10, Windows 8.1, Windows Server 2012 R2
The following sections describe key scenarios for KMS and MAK activation.
On this page
KMS scenarios
KMS can support simple, single-site networks and global networks. The following scenarios show:
The default implementation of KMS.
The implementation expanded to support a global network.
Default KMS implementation for a single-site network
Contoso has 100 Windows 7 Enterprise clients and a mixed set of Windows Vista, Windows Server 2008, and Windows Server 2008 R2 systems. Contoso is a flat domain (Contoso.com). The DNS server runs Microsoft DNS in its default configuration. This configuration supports DNS dynamic update protocol and DNS record scavenging to remove stale records.
Contoso purchases a license agreement that provides a KMS key, which will activate all of its systems. The information technology (IT) administrator installs Contoso’s KMS host key (CSVLK) on two KMS hosts running Windows Server 2008 R2 by using the following command run locally at an elevated command prompt:
The IT administrator then creates a Security Group in Active Directory® Domain Services (AD DS) named KMS_Hosts. The administrator adds the servers KMS_1 and KMS_2 to the KMS_Hosts membership.
The host KMS_1 is activated against Microsoft via the Internet: Slmgr.vbs /ato. KMS_1 automatically publishes its SRV resource records (RRs) to DNS. The IT administrator accesses the DNS server, locates the RR for _vlmcs._tcp.contoso.com, and changes its permissions to give KMS_Hosts Read, Write, and Delete permission to the record. The host KMS_2 is now activated against Microsoft via the Internet: Slmgr.vbs /ato.
Finally, the administrator confirms that the KMS host exclusion is enabled in Windows Firewall. The Key Management Service firewall exception needs to be enabled.
KMS clients on the Contoso network query DNS and receive the SRV records for both KMS hosts. The clients pick one or the other host and are activated (as soon as the KMS count rises above the threshold). See the section, “Activation Policy Values,” for more information about KMS count requirements.
KMS implementation in a complex, global network
Contoso has expanded into two domains, east.contoso.com and west.contoso.com. Network traffic can pass privately between the two networks through a firewalled wide area network (WAN) link. This link has limited bandwidth, so resources (including DNS) are replicated on both sides of the WAN link to reduce traffic when possible.
Contoso uses image-based deployment. Its client systems are standardized on Windows Vista, but the Windows Vista systems are being replaced by Windows 7 clients.
Users regularly travel geographically, and their network connection changes from one domain to the other. Clients’ IP addressing is provided dynamically by DHCP, including specifying the local DNS host, local gateway address, and so on.
To provide activation support for the existing Windows Vista clients and the new Windows 7 clients, Contoso installs four KMS hosts (using its KMS B key). Two KMS hosts are configured in east.contoso.com, and two are configured in west.contoso.com.
The IT administrator configures the KMS hosts so that the DNS SRV records drive Windows 7 and Windows Server 2008 R2 clients in the east domain to KMS_E1, if available, or to KMS_E2. If neither is available, the clients will attempt KMS_W1 and, finally, KMS_W2. Likewise, DNS in the west domain is configured so that Windows 7 clients in the west domain will prefer contacting KMS_W1, then KMS_W2 and only when these fail will attempt activation with KMS_E1 and KMS_E2 on the far side of the WAN link.
The IT administrator accomplishes this by making the following configuration changes (see Table 5):
KMS_E* hosts are added to the security group KMS_E. This group is given Read, Write, and Delete rights to the record _vlmcs._tcp.east.contoso.com.
KMS_W* hosts are added to the security group KMS_W. This group is given Read, Write, and Delete rights to the record _vlmcs._tcp.west.contoso.com.
DHCP servers are configured to add east.contoso.com and west.contoso.com to the DNS suffix search list for all clients.
Firewalls between east and west domains are configured to allow RPC traffic to the KMS hosts on port 1688.
Table 5. KMS Host Configuration
Description | Configuration | Host |
|---|---|---|
Configure east.contoso.com SRV priority and weight so that clients will contact KMS_E* hosts if available before trying KMS_W* hosts. Traffic will be divided: 75% to the KMS_*1 hosts and 25% to the KMS_*2 hosts. | HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionSoftwareProtectionPlatform DnsDomainPublishList= KMS_E1, 10, 75 KMS_E2, 10, 25 KMS_W1, 90, 75 KMS_W2, 90, 25 | KMS_E1 KMS_E2 |
Configure west.contoso.com SRV priority and weight so that clients will contact KMS_W* hosts if available before trying KMS_E* hosts. Traffic will be divided: 75% to the KMS_*1 hosts and 25% to the KMS_*2 hosts. | HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionSoftwareProtectionPlatform DnsDomainPublishList= KMS_W1, 10, 75 KMS_W2, 10, 25 KMS_E1, 90, 75 KMS_E2, 90, 25 | KMS_W1 KMS_W2 |
Then, the administrator confirms that the Windows Firewall exceptions are set to allow KMS client traffic and configures client computers, as Table 6 describes.
Table 6. KMS Client Configuration
Description | Configuration |
|---|---|
Disable KMS host caching | Slmgr /ckhc |
A customer URL is set to direct users with activation issues to the Contoso help desk | HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionSoftwareProtectionPlatformActivation AlternateURL = http://contoso.com/help |
The client reference computer is KMS activated, then sysprep /generalize is run. The system is shut down and imaged using ImageX from the Windows 7 Windows Automated Installation Kit (Windows AIK). The Windows AIK is available to download at https://go.microsoft.com/fwlink/?LinkId=136976.
MAK scenarios
The following sections describe scenarios for MAK activation. This section involves network and workgroup environments that are typical within large enterprises.
In the Core Network environment, all computers are within a common network managed by AD DS. The Secure Zone represents higher-security Core Network computers that have addition firewall protection.
The Isolated Lab environment is a workgroup that is physically separate from the Core Network, and its computers do not have Internet access. The network security policy states that no information that could identify a specific computer or user may be transferred out of the Isolated Lab.
MAK independent activation

The VAMT allows automation of MAK deployment and activation over the network by distributing MAKs from a centralized console. VAMT queries Microsoft activation servers to get the number of remaining activations for a given MAK, then lists the activation status of all MAK-activated systems in the environment. This count is a snapshot in time, not a real-time count. VAMT version 3.1 is included in the Windows ADK. For more information about VAMT, see Volume Activation Management Tool (VAMT) Technical Reference, and VAMT How-To Topics
In this scenario, the VAMT is deployed in the Core Network environment. The VAMT is installed on a central computer with network access to all client computers. Both the VAMT host and client computers have Internet access. The following instructions describe how to perform independent activation:
Install and launch the VAMT on a networked host computer:
Install the Windows ADK on the host computer.
Click Start, and then click VAMT to open the VAMT console.
Configure the Windows Management Instrumentation (WMI) firewall exception on target computers. Ensure that the WMI firewall exception has been enabled for all target computers.
Add computers to the computer information list (CIL):
On the VAMT console, click Action, and then click Add Computers to display the Add Computers dialog box.
Enter a Computer Group name such as Core Network Group to identify the group of computers you are activating.
Click the drop-down list to select a search option. You can search for computers in a workgroup, in an AD DS domain, or by individual computer name or IP address.
If you are searching by individual computer name or IP address, enter that information in the text box below the drop-down list.
If you are searching a domain or a workgroup, select the domain or workgroup from the additional drop-down list displayed for those options. Use the Filter by computer name field to search for a specific computer within the domain or workgroup.
Click OK.
The VAMT queries Active Directory Domain Services (AD DS) via Lightweight Directory Access Protocol (LDAP) and adds the computers it finds to the CIL.
Collect status information from the discovered computers:
For the VAMT to perform an action on a computer, it must have current license status data for that computer. Collect status from individual computers by directly selecting one or more computers in the computer list view pane. To perform operations for an entire group, in the tree view pane, select the Status Unknown node or the User Defined GroupsCore Network Group node.
Right-click the group or the desired computers, and then click Refresh Computer Status.
If you are activating computers that require administrator credentials different from the ones you are currently using, select Use Alternate Credentials.
Click OK.
Provide a Domain Administrator account (to collect status from all computers in the domain) and password when prompted.
The VAMT displays the Collecting computer information dialog box while it collects the status of all selected computers. When the process is finished, the refreshed status of each computer appears in the computer list view pane of the VAMT console.
Note
To retrieve the licensing status on the selected computers, the VAMT must have administrative permissions on the remote computers, and WMI must be accessible through Windows Firewall. In addition, for workgroup computers, a registry key must be created to enable remote administrative actions under User Account Control (UAC). For more information about configuring systems for VAMT remote management, see the VAMT help.
Add a MAK, and determine its remaining activation count:
Click Options, and then click Manage MAKs to open the Manage MAK Keys dialog box.
Click Add to enter a MAK.
Enter the MAK, and then click Validate.
Once validated, the Edition field is automatically populated.
Provide a meaningful description, and then click Add.
The MAK is now listed in the Manage MAK Keys dialog box.
Click Refresh remaining count to retrieve the number of remaining activations for the listed MAKs from Microsoft. (This step requires Internet connectivity.)
Click Exit to close the dialog box.
Install the MAK, and activate the client computers:
Select the computers to be activated, either by clicking a group in the tree view pane or by selecting individual computers in the list view pane.
Right-click the selected group or computers, and then click MAK Independent Activate to display the MAK Independent Activate dialog box.
Select the appropriate MAK from the Install MAK list.
Select the Install MAK (overwrite existing) and Activate Now check boxes to instruct the selected computers to activate immediately by contacting Microsoft Windows Activation over the Internet.
If an asterisk (*) appears next to the text for these check boxes, the action will apply only to applicable computers. For example, a computer installed with a Windows Vista retail edition cannot be activated using a MAK.
If you are activating computers that require administrator credentials different from the those you are currently using, select Use Alternate Credentials.
Click OK.
VAMT displays the Assigning Product Keys dialog box, and then displays the Activating Computers dialog box until it completes the requested action. If you selected Use Alternate Credentials, you will be prompted to enter the credentials prior to these dialog boxes.
MAK proxy activation
In this scenario, the VAMT is used to activate workgroup computers within an Isolated Lab environment. For workgroups such as this, which are completely isolated from the larger network, you can perform MAK proxy activation by installing a second VAMT on a computer within the isolated workgroup and using removable media to transfer VAMT CILs between that computer and another VAMT host that has Internet access. For more information about configuring systems for VAMT remote management, see the VAMT help. The following steps describe how to use the VAMT tool for proxy activation:
Install a VAMT on a workgroup computer in the Isolated Lab:
Install the Windows AIK on a host computer in the Isolated Lab workgroup.
This computer can be running Windows XP with Service Pack 2 (SP2), Windows Server 2003, Windows Vista, Windows 7, Windows Server 2008, or Windows Server 2008 R2.
Click Start, and then click VAMT to open the VAMT console.
Configure the Windows Management Instrumentation (WMI) firewall exception on target computers. Ensure that the WMI firewall exception has been enabled for all target computers.
Add computers to the CIL:
On the VAMT console, click Action, and then click Add Computers to open the Add Computers dialog box.
Enter a Group name such as Isolated Lab Group to identify the group of computers you are activating.
Select the Workgroup option, and specify the name of the workgroup, and then click OK.
The VAMT searches the workgroup for computers.
Note
For the VAMT to discover client computers in a workgroup, the network discovery Windows Firewall exception must be enabled.
Collect status from the discovered computers:
For the VAMT to perform an action on a computer, it must have current license status data for that computer. Collect status from individual computers by directly selecting one or more computers in the computer list view pane. To perform operations for an entire group, in the left pane, select the Status Unknown node or the User Defined GroupsIsolated Lab Group node.
Right-click the group or the desired computers, and then click Refresh Computer Status.
If you are activating computers that require administrator credentials different from the those you are currently using, select Use Alternate Credentials.
Click OK. When prompted, provide the credentials for an account that has local administrative rights on the selected workgroup computers.
The VAMT displays the Collecting computer information dialog box while it collects the status of all selected computers. When the process is finished, the refreshed status of each computer appears in the computer list view pane of the VAMT console.
Note
To retrieve the licensing status on the selected computers, the VAMT must have administrative permissions on the remote computers, and WMI must be accessible through Windows Firewall. In addition, for workgroup computers, a registry key must be created to enable remote administrative actions under UAC.
Add a MAK:
Click Options, and then click Manage MAKs to open the Manage MAK Keys dialog box.
Click Add to enter a MAK.
Enter the MAK, and then click Validate.
Once validated, the Edition field is automatically populated.
Provide a meaningful description, and then click Add.
The MAK is now be listed in the Manage MAK Keys dialog box.
Click Exit to close the dialog box.
Note
Because the VAMT is not installed on a computer with Internet access, the Refresh Remaining Count option will not operate. This feature requires Internet access.
Install the MAK on the Isolated Lab computers:
Select the Isolated Lab group in the tree view pane.
Right-click the selected group, and then click MAK Proxy Activate to display the MAK Proxy Activate dialog box.
Select the appropriate MAK from the Install MAK list.
Select Install MAK (overwrite existing).
If an asterisk (*) appears next to the text for this checkbox, the action will apply only to applicable computers. For example, a computer installed with a Windows Vista retail edition cannot be activated using a MAK.
Clear the Get Confirmation ID from Microsoft check box, because this computer does not have Internet access.
Clear the Apply Confirmation ID and Activate check box, because confirmation IDs (CIDs) have not yet been requested.
If you are activating computers that require administrator credentials different from the those you are currently using, select Use Alternate Credentials, and then click OK.
VAMT displays the Assigning Product Keys dialog box until it completes the requested action. If you selected Use Alternate Credentials, you will be prompted to enter the credentials prior to this dialog box.
Note
Selecting the Install MAK (overwrite existing) check box force-installs a MAK on a client computer. This must be done with care. If the pre-SP1 version of Windows Vista has been installed on the computer for more than 30 days, then its Initial Grace period has expired, and the computer will enter Reduced Functionality Mode (RFM) if activation is not completed successfully before the next logon. However, you can use MAK proxy activation to recover properly configured computers from RFM as long as the computers are accessible to the VAMT host. RFM only applies to the pre-SP1 version of Windows Vista. Windows Vista with SP1 or later, Windows 7, Windows Server 2008, or Windows Server 2008 R2 will not enter RFM.
Save the CIL:
In this step, the full CIL is saved on the local (that is, workgroup) VAMT host. In MAK proxy activation, it is critical to retain this file, because the VAMT uses it to apply the CIDs to the proper computers.
Using the VAMT tree view or list view pane, select the group or the individual computers that successfully received a MAK.
From the File menu, click Save to display the Save the Computer Information List dialog box.
Select a directory, and then enter a CIL file name such as IsolatedLabGroup.CIL.
Click Save.
Export the CIL:
As stated previously, the enterprise’s security policy states that no information that could identify a specific computer or user may be transferred out of the Isolated Lab. Therefore, this type of data must be excluded from the CIL file to be transferred to the Core Network VAMT host.
Using the VAMT tree view or list view pane, select the group or the individual computers that successfully received a MAK.
Right-click the selected group or computers, and then click Export Computers to display the Save the Computer Information List dialog box.
Select Exclude any sensitive environment data.
Click Browse to display the Save As dialog box.
Select a directory, and then enter a CIL file name such as IsolatedLabGroupSecureExport.CIL.
Click Save.
Copy the IsolatedLabGroupSecureExport.CIL file to removable media (disk drive, CD/DVD, or USB flash drive [UFD]).
Note
Selecting the Exclude any sensitive environment data check box excludes Personally Identifiable Information (PII) from being saved in the CIL. As a result, the CIL must be re-imported in this VAMT host and into the full-save CIL file so that the CIDs requested from Microsoft can be correctly assigned to the computers in the Isolated Lab group.
Import the CIL on a VAMT host with Internet access:
Copy IsolatedLabGroupSecureExport.CIL from the removable media to a drive on a VAMT host that has Internet access.
Open the VAMT console.
From the File menu, click Import to open the Open Computer Information List dialog box.
Locate and select IsolatedLabGroupSecureExport.CIL and then click Open to load the CIL into the VAMT.
Confirm that the computer, group, and workgroup names are not visible.
Request CIDs from Microsoft:
Right-click the imported computers, and then click MAK Proxy Activate to open the MAK Proxy Activate dialog box.
Clear the Install MAK (overwrite existing) check box.
Clear the Get Confirmation ID from Microsoft check box.
Clear the Apply Confirmation ID and Activate check box, because this VAMT host is not on the same network as the selected computers.
Click OK.
The VAMT displays the Acquiring Confirmation ID online dialog box while it contacts Microsoft and collects the CIDs.
Export the CIL from the Internet-connected VAMT host:
After the CIDs have been retrieved for all computers, save the CIL file. In the VAMT console, scroll to the right and confirm that the PendingCID column has values.
From the File menu, click Save As, and provide a new name for the file, such as IsolatedLabGroupSecureExportwithCID.CIL.
Copy the updated file IsolatedLabGroupSecureExportwithCID.CIL to removable media (disk drive, CD/DVD, or UFD).
Import the CIL on the original VAMT host within the Isolated Lab:
Copy IsolatedLabGroupSecureExportwithCID.CIL from the removable media onto a drive on the VAMT host in the Isolated Lab.
Open the VAMT console.
From the File menu, click Open to display the Open Computer Information List dialog box.
Locate and select IsolatedLabGroup.CIL, and then click Open to load the CIL into the VAMT.
This displays the previously discovered computers and their license states in the computer list view pane.
From the File menu, click Import and browse to the file that contains the CIDs (IsolatedLabGroupSecureExportwithCID.CIL).
This starts the merge process that matches the CIDs to the computers’ IIDs.
From the File menu, click Save, and then enter a file name such as IsolatedLabGroupwithCID.CIL to save this file that associates the IIDs with the corresponding CIDs.
Important
Saving this file is critical for reimaging scenarios. It is strongly recommended that you back up this file and protect it from being overwritten.
Apply the CIDs, and activate the Isolated Lab computers:
Right-click the Isolated Lab group in the tree view pane, and then click MAK Proxy Activate to open the MAK Proxy Activate dialog box.
Clear the Install MAK (overwrite existing) check box, because the selected computers already have a MAK installed.
Clear the Get Confirmation ID from Microsoft check box.
Select the Apply Confirmation ID and Activate check box to instruct the VAMT to activate the selected computers by installing their CIDs.
Click OK.
The VAMT displays the Assigning Confirmation IDs dialog box while it installs the CIDs on the selected computers.
Optionally, reactivate reimaged computers in the Isolated Lab:
If the computers in the Isolated Lab have been reimaged but the underlying hardware has not changed, the VAMT can reactivate them using the IsolatedLabGroupwithCID.CIL file.
Redeploy Windows to each computer using the same computer names as before.
Open the VAMT console on the local (workgroup) VAMT host.
From the File menu, click Open, and then select the IsolatedLabGroupwithCID.CIL file.
In the tree view pane, right-click the Isolated Lab group, and then click Reapply Confirmation ID to display the MAK Proxy Reactivate dialog box.
Leave the Install MAK (overwrite existing) check box selected, and ensure that the previously used MAK is selected from the list.
Leave the Reapply Confirmation ID and Reactivate check box selected to reapply the stored CIDs from the IsolatedLabGroupwithCID.CIL file.
Leave the Require exact IID match check box selected if the hardware has not changed since the initial MAK Proxy Activation and you are using the same MAK to reactivate the computer.
Clear this check box if the hardware has changed but you would still like VAMT to attempt a reactivation using the previously stored CID. Note that Windows might not be successfully reactivated in this scenario.
If you are activating a computer that requires administrator credentials different from those you are currently using, select the Use Alternate Credentials check box.
Click OK.
The VAMT displays the Assigning Product Keys dialog box while it applies the MAK to the Isolated Lab Group.
The VAMT displays the Assigning Confirmation IDs dialog box while it installs the CIDs on the selected computers.
Note
Selecting the Install MAK (overwrite existing) check box force-installs a MAK. This must be done with care. If the pre-SP1 version of Windows Vista has been installed for more than 30 days, then its Initial Grace period has expired and it will enter RFM if activation is not completed successfully before the next logon. VAMT can be used to recover properly configured remote computers from RFM as long as they are accessible on the network. RFM only applies to the pre-SP1 version of Windows Vista. Windows Vista with SP1 or later, Windows 7, Windows Server 2008, and Windows Server 2008 R2 will not enter RFM.
VAMT support for KMS activation
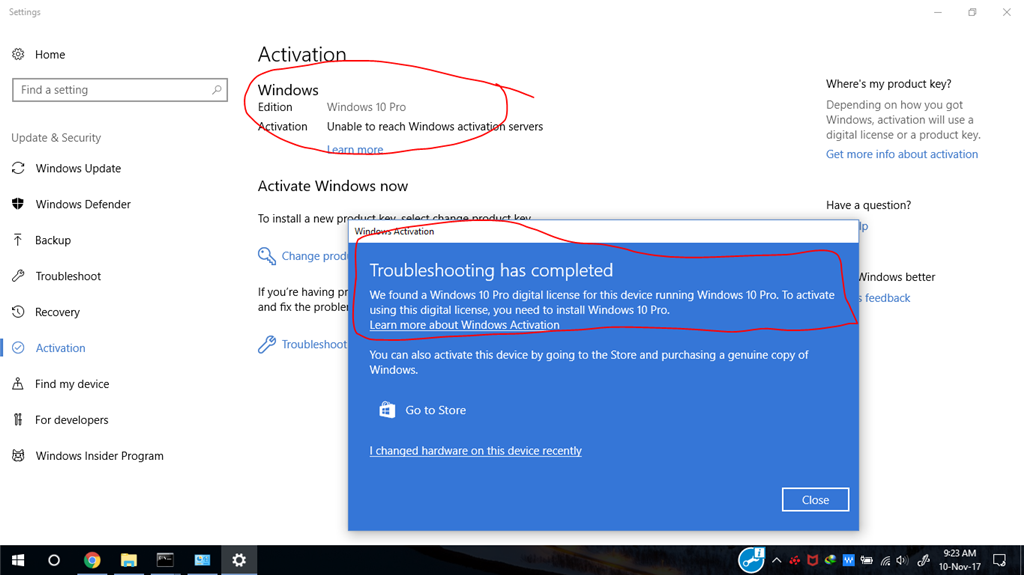
Error Code 0xc004d302
In this scenario, the VAMT is used to install and activate KMS client keys on either Core Network or Isolated Lab computers. The procedure described below assumes that the VAMT has been installed and the computers have been added to the CIL. These tasks are described in steps 1–4 in either Scenario 1 (for the Core Network) or Scenario 2 (for the Isolated Lab workgroup).
Open the VAMT console.
Select the computers to be activated, either by clicking a group in the tree view pane or by selecting individual computers in the list view pane.
Right-click the selected group or computers, and then click Configure for KMS Activation to display the KMS Configuration dialog box.
Select Install KMS Client Key (overwrite existing) to instruct the VAMT to install a KMS client key on a client computer.
Select the appropriate activation option:
Auto-Discover KMS host using DNS. The VAMT first clears any previously configured KMS host on the target computer, then instructs the computer to query DNS to locate a KMS host and attempt activation.
Use specific KMS host and port. The VAMT sets the specified KMS host name and port on the target computer, and then instruct the computer to attempt activation with that specific KMS host.
If you are activating computers that require administrator credentials different from those you are currently using, select the Use Alternate Credentials check box, and then click OK.
The VAMT displays the Assigning Product Keys dialog box, and then displays the Activating Computers dialog box until it completes the requested action. If you selected the Use Alternate Credentials check box, you will be prompted to enter the credentials prior to these dialog boxes.
Converting KMS to MAK activation
Windows 7 and Windows Server 2008 R2 install automatically as KMS clients. To convert a KMS client to MAK activation, install a MAK. A MAK can be installed during or anytime after operating system installation.
A MAK key can be installed on a reference image of Windows 7 and Windows Server 2008 R2 to make all installations from that image use MAK activation instead of the default KMS activation. Doing so alleviates the need to specify a MAK in an unattended installation file.
Installing a MAK during operating system installation
You can convert a KMS client to a MAK client during the initial installation of Windows 7 or Windows Server 2008 R2 by including a MAK in an unattended setup (Unattend.xml) file. The Unattend.xml file can be used with Setup.exe or Windows Deployment Services. For more information, see the Unattended Windows Setup Reference help file in the Windows AIK at https://go.microsoft.com/fwlink/?LinkId=136976.
Note
The MAK is stored in clear text in the Unattend.xml file. During an unattended installation, the file Unattend.xml or AutoUnattend.xml is copied to the %SystemRoot%Panther folder of the target computer. However, at the end of the Setup process, the Setup program replaces it with “SENSITIVEDATADELETED.”
Installing a MAK after operating system installation
You can configure a volume edition of Windows 7 or Windows Server 2008 R2 to use MAK activation by using the Control Panel System item or by running the Slmgr.vbs script:
To install a MAK by using System Center, click the Change your product key link, and then type the MAK in the Change your product key for activation dialog box.
To install a MAK by using Slmgr.vbs, run the following command at a command prompt:
where MultipleActivationKey is the MAK.
If users install a MAK by using the user interface (UI), the MAK client attempts to activate itself over the Internet one time. If the users install a MAK key by using the Slmgr.vbs script, the MAK client does not try to activate automatically. The user can use Slmgr.vbs /ato to manually activate the MAK over Internet.